Get the latest news delivered right to your email.
2024 Election
Top Stories
Advertisement
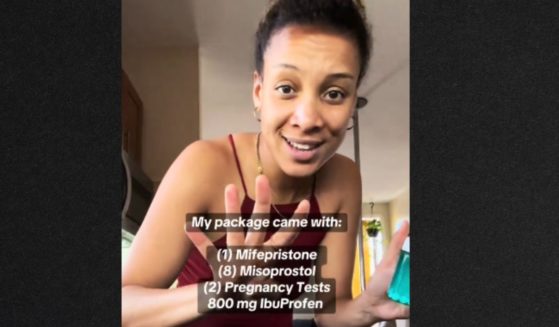
Watch: Woman's How-To Video on Abortion Goes Wrong When People Notice What's in Background
Viewers were shocked at what they saw in the background of a TikTok user's tutorial video on how to perform an at-home abortion.
By Anthony Altomari
April 24, 2024
Comment
MoreShare
“Numbers made up”,“Someone's cooking the books” - Reaction to Biden's Economic Numbers
Some are reacting with incredulity at the number the Biden administration is floating to tout his economic record.
By Warner Todd Huston
April 24, 2024
Comment
MoreShare
Watch: Abortion Advocate Desperately Tries to Interrupt Pastor's Prayer at Capitol, Fails Miserably
Not even a shrieking abortion advocate could drown out the power of prayer or the truth of God's promise to terrified young pregnant women.
By Michael Schwarz
April 24, 2024
Comment
MoreShare
Fight Breaks Out with Harris' Secret Service Detail - Agent Handcuffed, Removed from Scene
News reports indicate a Secret Service agent assigned to VIce President Kamala Harris went bonkers on Monday.
By Jack Davis
April 24, 2024
Comment
MoreShare
With Lowest Oil Reserves Since '83 and Skyrocketing Prices, Will Biden Do the Unthinkable?
Oil reserves are half empty, Biden's not refilling them. But summer's coming, and we'll need gas. Guess where Biden will get it.
By Mike Landry
April 24, 2024
Comment
MoreShare
Report: Family Outraged at Disney World - Realized the Evil Queen 'Actress' They Took Pics with Was a Man
A father was outraged when it appeared that Walt Disney World reportedly hired a man to interact with children as the Evil Queen.
By Allison Anton
April 24, 2024
Comment
MoreShare
'This Is Vile': Biden Comes Under Fire for Invoking Jesus While Promoting Abortion
The Apostle Paul wrote 2,000 years ago that Christians must pray for their political leaders. This is a great example of why.
By George C. Upper III
April 24, 2024
Comment
MoreShare
Watch: Biden Admits 'We Can't Be Trusted' in Latest Major Blunder
Watch the clip with YouTube's closed captioning on, and you'll see that even its talk-to-text AI recognized what Biden said here.
By George C. Upper III
April 24, 2024
Comment
MoreShare
Advertisement
'Woman': The Left's Absurd Quest to Redefine the Term
The question “What is a woman?” is perfectly leveraged to produce absurdity because to pose this question is absurd.
Comment
MoreShare
Biden Breaking the Ten Commandments: Part Four - Bidenomics Subverts the Sabbath
Biden is upsetting the balance of rest and work ordered by God — and Americans are paying the price economically and spiritually.
Comment
MoreShare
Former Military Chaplain Talks Becoming Battle-Ready to Serve in God's End-Times Army
U.S. Army Col. (Ret.) David Giammona believes the world is entering the end times, and "the Lord wants us to work even harder."
Comment
MoreShare
Advertisement